With Qualy, you can receive tuition and other fees, easily reconcile in your bank, get schools and agents paid automatically, and follow along in a beautiful real-time dashboard.







It's never been so easy to collect student payments and pay our partners. Qualy takes care of all comms and docs involved on the payment process, with no need for systems integration.
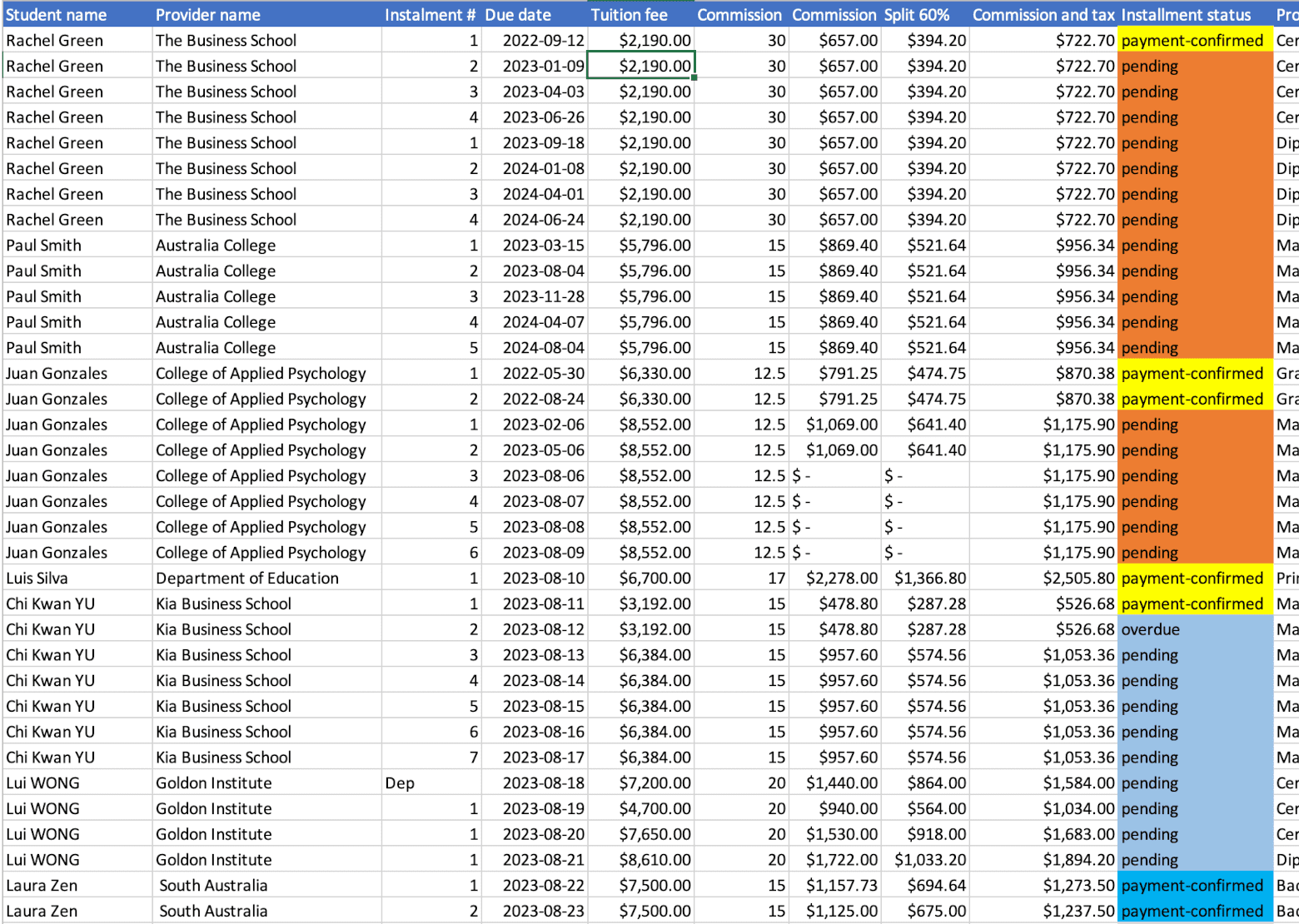
Use Qualy to help manage it, or control everything in real-time via the Qualy dashboard. You can continue using your current spreadsheet, or rely 100% on Qualy.
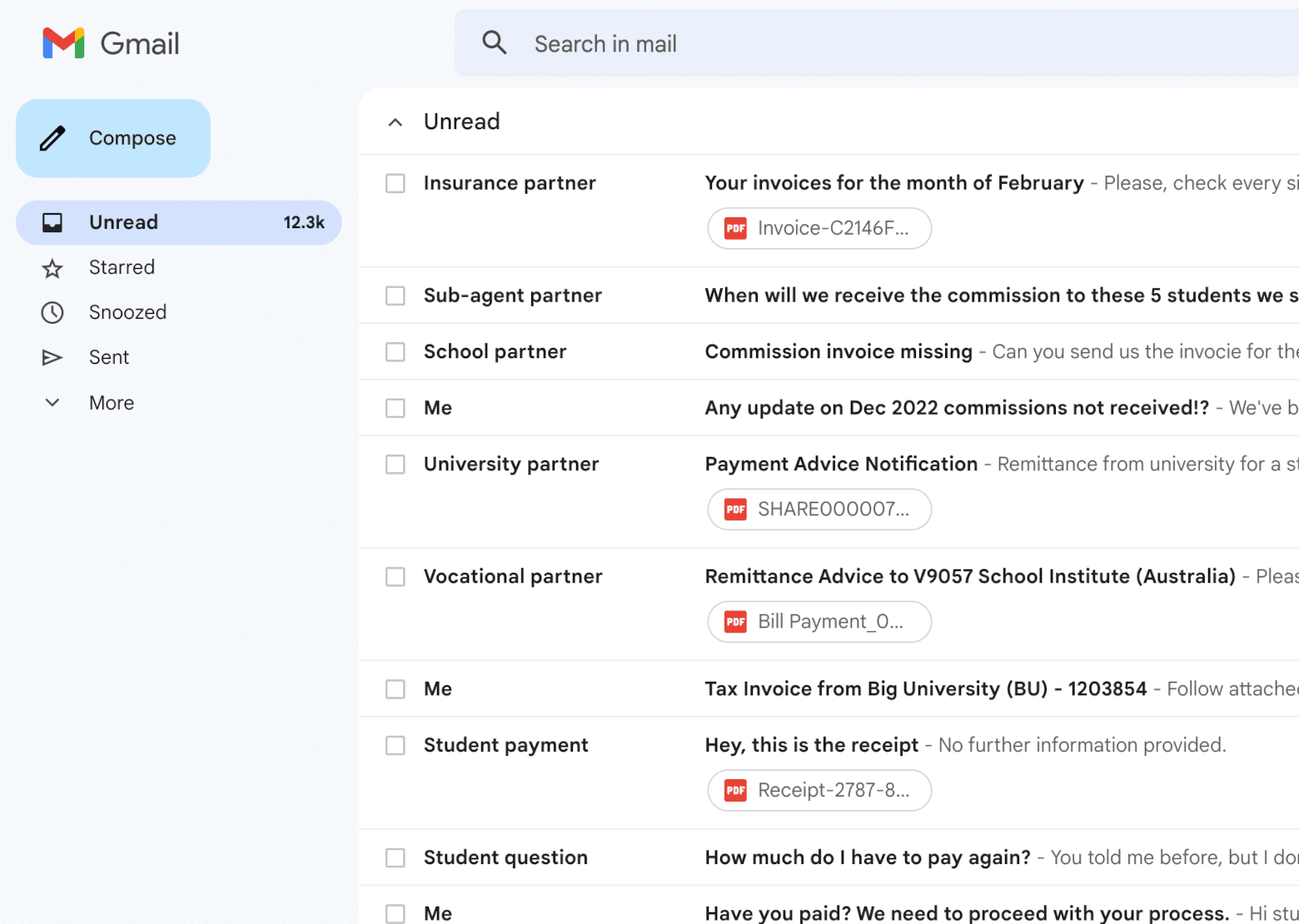
Qualy will automatically remind students of payments before and after they are overdue, send receipts and create invoices automatically.
Qualy is a drop-in, turn-key solution. Continue using the same tools. It can work alongside Excel, Xero, Quickbooks, NetSuite, and any other software.
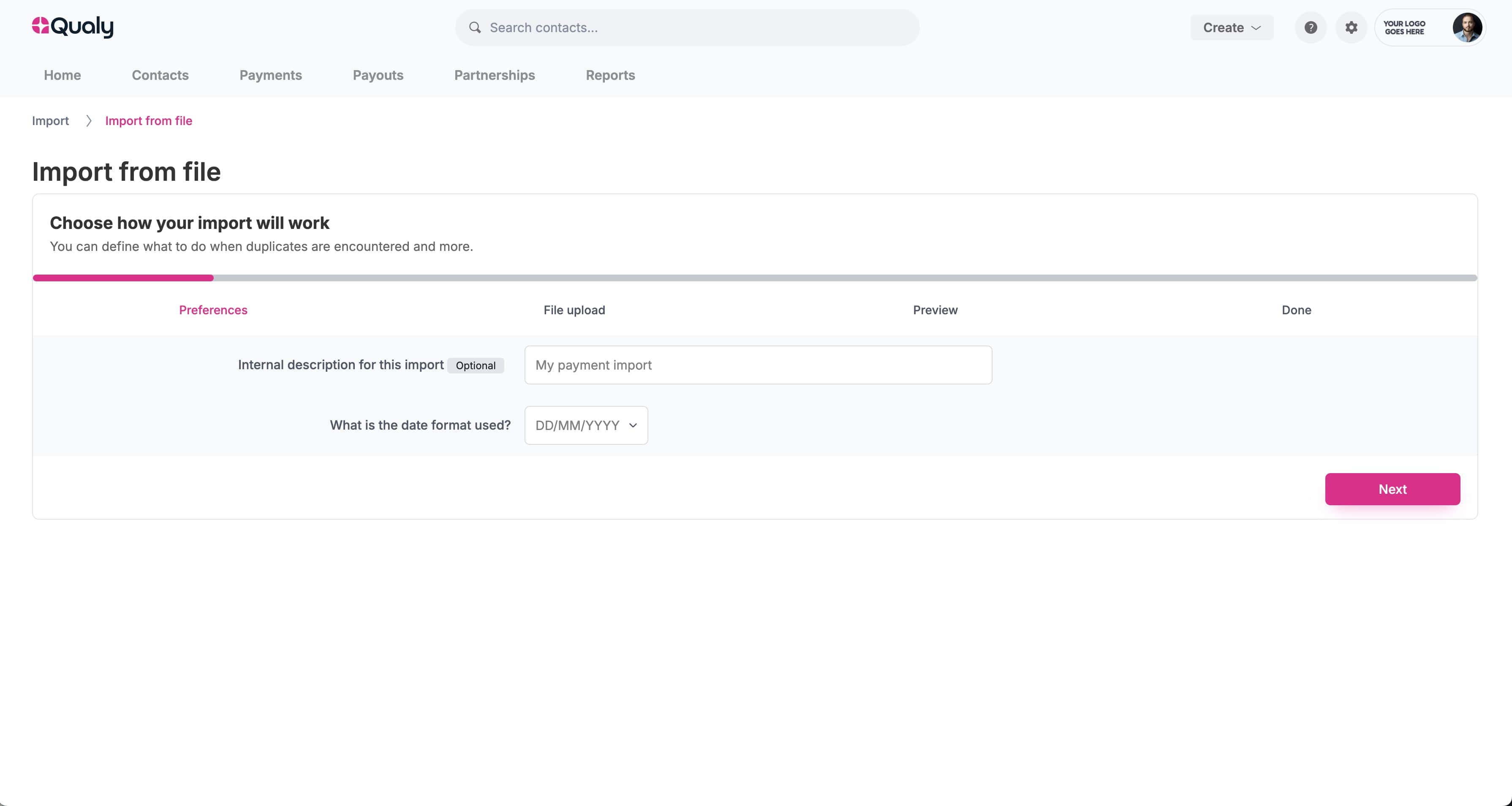
Qualy is a drop-in solution. It can work alongside Excel, Xero, Quickbooks, and more.
RTO Manager
Coming soon
Coming soon

Qualy has improved our student payment experience and reduced the time & money we spend on finance related admin.
Dan Wortley
CEO of Universal English College
Provide a simple and fast way for students to pay. They can pay on the move and with multiple payment options. Payment receipts are sent after each payment to reduce your admin workload.
Get clear oversight across current, pending and overdue payments in real time. Filter to view partner performance and check your revenue projection to support your financial planning.
With custom statement descriptors and unique reference numbers you will always know who to allocate payments to. This is the end of unreconcilable deposits.
Qualy will take a payment from a student, process the sales commission and have the funds available in each receiving account in under 10 seconds. 365/7. No more delays and waiting.
Our system can work with the most complicated payout structures. You can decide to split the received payment as many times as you like. Our system can split tuition fees, as well as OSHC, enrolment & material fees.
Qualy helps you with your debt management. Save time chasing overdue payments, by deciding how and when you wish to follow up with students.
Qualy was designed for collecting payments for the international education industry. It helps colleges, schools, and education agents of all sizes.


